
Data Loss Prevention: The Secret Weapon Businesses Need
Don’t let a data breach cripple your business. Our guide to Data Loss Prevention (DLP) reveals the secrets to stopping data leaks and keeping your information safe.
Your London Telecoms and IT partner


A cyber attack is the last thing that any business wants to encounter. The word ‘cyber attack’ itself is somewhat taboo and of course comes with many negative connotations. However, with the number of businesses falling victim to cyber attacks increasing each year, it’s vitally important that businesses have processes in place to minimise the risk.
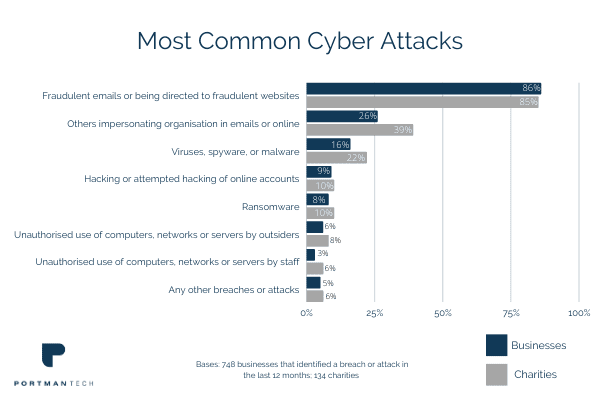
Almost half of businesses (46%) and a quarter of charities (26%) report having cyber security breaches or attacks in the last 12 months.
Official Statistics Cyber Security Breaches Survey 2020
Being the victim of a cyber attack is not necessarily a direct result of having poor security in place. Hackers can be extremely clever in exploiting vulnerabilities through an array of different techniques.
Don’t let cyber threats stifle your ambition. Grow with confidence with our comprehensive cyber security services. Our proactive approach safeguards your data, allowing you to focus on scaling your business without fear.
Some businesses will have IT departments whose responsibility is to ensure there is a cyber security strategy in place, however that isn’t the case for all businesses. Therefore, it is equally important for business owners to be aware of the potential threats, as well as ways to improve both organisational and individual habits to reduce the potential risk of a cyber attack.
Unfortunately it’s not possible to guarantee that you won’t fall victim to a cyber attack at some point, but we’ve listed a few ways below that can help to reduce the risk.
It may seem obvious, right? But, it is still critical to mention. Particularly as the most popular password of 2020 was ‘123456’, which according to NordPass takes less than a second to crack. Coming fourth in the list of most popular passwords to use was ‘password’, also taking less than a second for hackers to crack.
An ideal strong password should be a combination of numbers and characters, and should also be unique. Some businesses put ‘password policies’ in place for employees, in order to ensure employees are using secure passwords where necessary.
Other technical solutions can help minimise the risk of exposure, such as multi-factor authentication and password deny lists (preventing common passwords from being used) as well as single sign-ons, which can reduce the need for passwords.
Cyber attacks can sometimes be the result of out of date or not fully functioning software, which is where patch management can come into play.
Essentially patch management is the process of scanning devices across networks for any missing or out of date software, and fixing the problem with “patches”. If updates to servers, firewalls or networks are not actioned, systems are left vulnerable to attack.
There are many different types of patch management software available and choosing the right one essentially comes down to the needs of the business. Both individual teams and automated software can provide the required solution, to identify and repair any potential vulnerabilities or flaws after a software or application release.
It may not be necessary for employees to have all levels of access on their devices used for company work. For example, while they may need the option of accessing specific software, they likely don’t need the option of downloading other forms of software.
Managing user privileges, such as restricting IT admin and access rights for specific users, will mean that they are unable to install software or access certain data on the network, which can help to reduce the risk of any potential threats.
Phishing scams can be one of the most common threats both to businesses and individuals, and are becoming increasingly more sophisticated.
Often sent through email or messaging apps, the attacker will pose as a legitimate business or trusted entity (they could even pretend to be another member of staff). The core aim is to trick the recipient into believing that it is a credible form of contact, encouraging them to click on a link or open an attachment.
As phishing emails are becoming increasingly more intelligent, there are certain signs to look out for as well as methods to protect yourself and your business from falling victim.
Spam filters on email software can be an effective way to keep phishing emails out of your inbox. It’s also possible to implement labels on emails, so that they are instantly flagged as being from an external party. This could be particularly useful if a phishing scam is posing as a co-worker or other employee.
While the above ways can all help to minimise the risk of a cyber attack, it ultimately comes down to being vigilant.
It’s important that everyone in the business understands the potential risk of a cyber attack, not just business owners or IT teams.
Feeling like a sitting duck for cyberattacks? Worried about data breaches and downtime? Our cyber security services identify and fix vulnerabilities before they become a nightmare. Sleep soundly knowing your business is protected.
At Portman Tech we can provide bespoke user training for businesses to raise awareness of possible phishing attacks, including examples of potential risks and what employees should look out for.
If this is something that you would like some advice or guidance on, please feel free to get in touch with our friendly team.
We’ve provided many businesses with bespoke IT support, including specific cyber security strategies for finance.
ABOUT THE AUTHOR

Vikas Shah joined Portman Tech as Chief Technology Officer in 2018. IT has always been his passion and he has built his career around technology. Vikas closely follows developments in technology, providing clients with solutions that fit their requirements.

Don’t let a data breach cripple your business. Our guide to Data Loss Prevention (DLP) reveals the secrets to stopping data leaks and keeping your information safe.

Worried about online threats? Our guide to internet security in 2024 will show you how to protect yourself from hackers, malware, and data breaches. Browse safe and secure today!

Explore key concepts, principles, and best practices to protect your valuable information. For comprehensive information security management solutions in London.

0800 862 0120
hello@portmantech.com
123 Aldersgate Street, London EC1A 4JQ